Since January 1, 2025, manufacturers of digital health applications (DiGA) must prove compliance with data security requirements by means of an official certificate. The basis for certification is BSI TR-03161, which was first published in 2020.
The BfArM checks certification as a fixed requirement for listing an application in the DiGA directory. No new DiGA will be accepted without a valid certificate. Listed DiGA also face removal from the directory without certification (however, there is currently no deadline for listed DiGA).
Many manufacturers underestimate the extensive implications of this certification and how complex the testing process is.
With this article, we would like to provide (prospective) DiGA manufacturers with a structured overview:
- What exactly does TR-03161 require?
- How does certification with the testing center and BSI work?
- What are the associated costs and how long does such certification take?
- What are the practical implications of BSI TR-03161 for DiGA?
- What does the future hold for BSI certification? (Keyword: BSI TR-03185)
Based on our practical experience from several TR-03161 projects, we describe the current status of certification requirements.
Table of Contents
- 1. Who does BSI TR-03161 apply to?
- 2. Requirements and Structure of BSI TR-03161
- 3. The Certification Process
- 4. Costs and Time Frame of the Certification Process
- 5. Validity Period & Recertification according to BSI TR-03161
- 6. BSI TR-03161 Certificate with Conditions
- 7. Changes to Certified Products – BSI TR-03185
- 8. Practical Implications for DiGA
- 9. Mandatory Penetration Testing for DiGA
- 10. BSI TR-03161 vs. ISO 27001
- 11. Criticism of the Process
- 12. Important Links and Resources
- 13. Future Outlook for BSI TR-03161 and DiGA Data Security Certification
- 14. Conclusion
1. Who does BSI TR-03161 apply to?
The TR-03161 can generally be used for many applications in the German healthcare sector that process sensitive data.
However, it is primarily legally binding for digital health applications (DiGA) in accordance with Section 139e of the German Social Code, Book V (SGB V) and digital care applications (DiPA) in accordance with Section 78a of SGB XI. An official certificate must be presented for these products from January 1, 2025.
This article focuses on DiGA, as certification requirements currently have the greatest practical relevance in this area.
For certification according to BSI TR-03161, please note:
- It can be applied regardless of the risk class.
- It includes all components of the application (i.e., app, backend, web portal, and patient and practitioner access).
- Even if hosting or infrastructure is outsourced to external cloud providers, these components must comply with the requirements of BSI TR-03161. At the same time, server providers must have a Type 2 C5 certificate.
- New digital health applications already require certification in accordance with BSI TR-03161 in order to be included in the digital health application directory.
- For DiGA already listed at this point in time, the BfArM currently still tolerates the absence of a certificate as long as the manufacturer can prove that it is in the process of certification. However, this may change at any time.
Note: For the sake of simplicity, we refer to the product of a (prospective) DiGA manufacturer in this article as “DiGA,” regardless of whether it is already listed or not. Of course, not every application is listed as a DiGA as soon as it begins the certification process according to BSI TR-03161.
2. Requirements and Structure of BSI TR-03161
Technical Guideline TR-03161 defines the minimum requirements for data security for digital health and care applications. It thus forms the basis for the legally required data security certification in accordance with Section 139e of the German Social Code, Book V (SGB V) and Section 78a of the German Social Code, Book XI (SGB XI).
IT security in general and BSI TR-03161 in particular, essentially pursue three protection goals: confidentiality, integrity and availability. The standard specifies concrete measures that you, as a manufacturer, must take to ensure that sensitive data remains confidential, intact and available.
- Confidentiality means that only authorized persons or systems may access sensitive data. Unauthorized persons may not view or read data, either in the app or during transmission.
- Integrity ensures that data remains accurate and unchanged. Manipulation or unintentional changes are prevented or clearly identified.
- Availability means that applications and data can be used reliably. Failures or interruptions are minimized through appropriate technical and organizational measures.
2.1 Structure of BSI TR-03161
TR-03161 consists of three parts that together cover all security-related components of a digital health application. Each part focuses on a specific system level and formulates specific requirements that are later checked individually in the certification audit. This results in a complete security model that secures the app, web front end and back end equally.
The three parts of the guideline cover all technical components of a DiGA. The app, web front end and back end are each tested and certified separately.
- Part 1: Mobile Applications (Apps): Part 1 describes the security requirements for mobile applications (such as iOS and Android). It specifies how apps may process sensitive data, how they may use device functions and how they must be protected against manipulation.
- Part 2: Web Applications: Part 2 addresses web-based components (e.g., a web interface that a practitioner or patient can access in a browser). This part describes how web applications are executed securely in the browser and how typical web vulnerabilities must be prevented.
- Part 3: Backend Systems: Part 3 defines the requirements for server-side components, regardless of whether they are operated on-premises or in the cloud. Since sensitive health data is usually processed centrally, this part contains particularly comprehensive specifications regarding architecture and operation.
It is important to note that for each DiGA, an individual decision is made as to which of these three parts apply to the product. For example, a web application with a backend server only needs to comply with parts 2 and 3 and does not consider Part 1 (for mobile applications) as part of the certification process.
2.2 Scope: Product and Processes
The structure of the guideline follows a clear system based on a so-called security problem definition. This includes:
- Assumptions about browsers, end devices and backend infrastructure
- Defined threat scenarios such as unauthorized access, data manipulation, exploitation of debug functions, or misconfigurations
- Organizational security guidelines that the manufacturer must implement, for example: security lifecycle, patch management, disclosure of the purpose of data processing, processes for reporting vulnerabilities
TR-03161 therefore considers not only technical implementation (source code and product), but also processes and documentation. A product-related pen test is therefore not sufficient for certification. The manufacturer’s processes and documentation are also reviewed.
2.3 Test Aspects
The guideline structures all requirements into test aspects. Each test aspect contains specific rules marked with MUST, SHOULD, MAY or MUST NOT.
Each part of BSI TR-03161 contains 11 (in parts 1 and 2) or 10 (in part 3) test aspects:
- Intended use
- Architecture
- Source code
- Third-party software
- Cryptographic implementation
- Authentication and authorization
- Data security
- Paid resources
- Network communication
- Organizational security (only for Part 3 – Background systems)
- Platform-specific interactions (only for parts 1 and 2 – mobile & web)
- Resilience (only for parts 1 and 2 – Mobile & Web)
Tip: Copy a list of the individual test aspects of each part of TR-03161 into your documents and check them off in a structured manner, one after the other. This is a helpful project management tool for your development team.
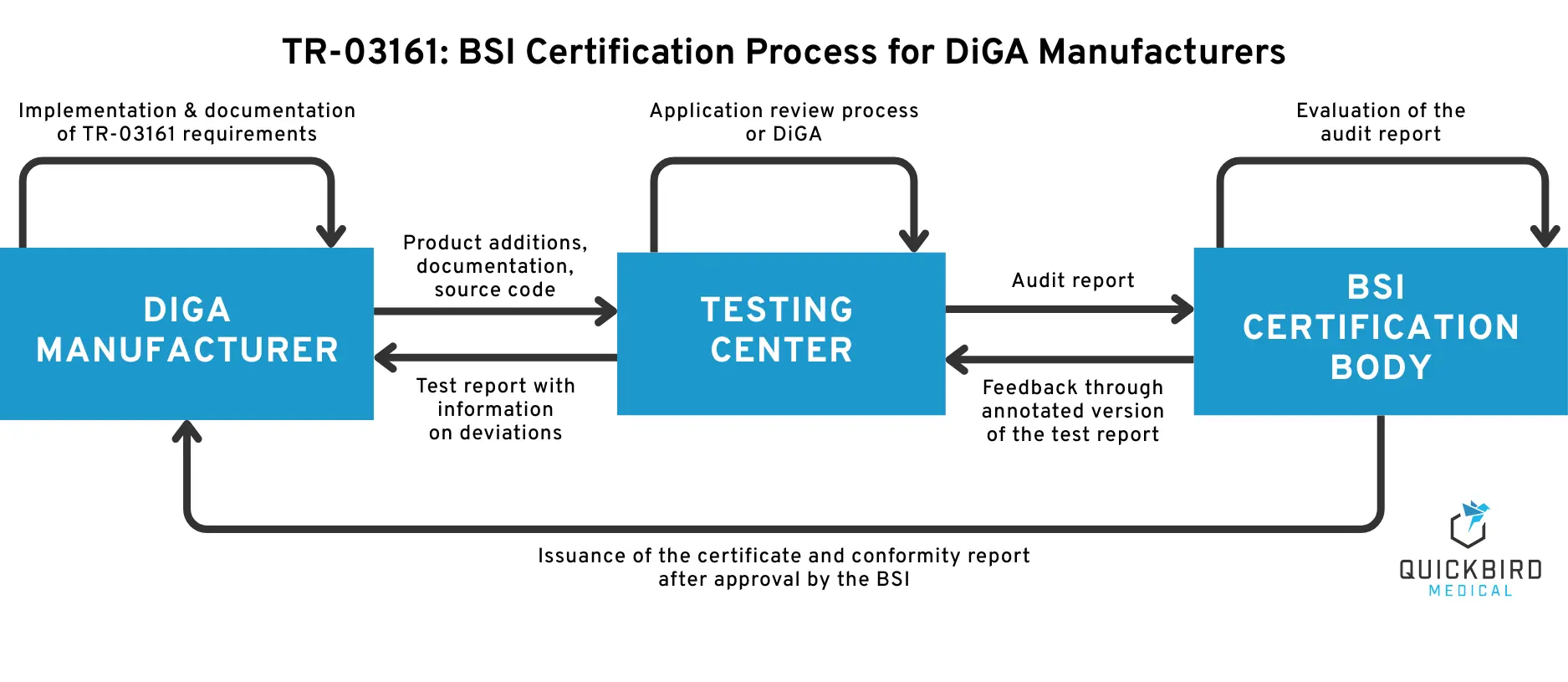
3. The Certification Process
The entire certification process for a DiGA consists of three phases:
- Preparation phase: As a DiGA manufacturer, you prepare for the testing process. You familiarize yourself with the BSI TR-03161 standard and implement the requirements to the best of your knowledge within your product and processes. You also look for a testing center for certification, establish the contractual basis for cooperation with it and reserve a test date.
- Test phase: Once you have completed the implementation of the TR requirements on your side, send your documentation, product access details and software source code to the testing center. The testing center will begin the testing process and send you the test report, including any deviations, once the test has been completed. Whether you receive interim feedback or other communication depends on the testing center in question. If the testing center is satisfied with all aspects, it will prepare the test report for submission to the BSI.
- Certification phase: The BSI certification body receives the final test report from the testing laboratory and evaluates whether it can give a positive assessment of the certification on this basis. If so, you will receive the certificate including the conformity report from the BSI. If not, the BSI will return an annotated list of the test report to the testing agency. The testing agency will evaluate the feedback and forward the deviations relevant to you as a manufacturer to the DiGA manufacturer for implementation.
Note: The testing agency refers to a private companywhich has been officially accredited by the BSI to test this technical guideline. A list of testing agencies can be found below in this article. Certification body, on the other hand, refers to the department at the BSI that is responsible for certification and makes the final decision in this regard.
We have also outlined the certification process in simplified form in the following illustration.
BSI Certification Process for DiGA Manufacturers according to TR-03161
4. Costs and Time Frame of the Certification Process
4.1 Costs of the Certification Process
For internal budget planning, you should anticipate the following cost packages:
- The costs of the testing center: The work carried out by the certification body naturally incurs costs. The amount of these costs varies between certification bodies and also depends on your product and the scope of the testing. We recommend that you obtain several quotes so that you can compare them.
- The costs for the BSI: What may be less obvious is that the BSI will also send you an invoice after the certification process has been completed. Incidentally, this happens regardless of whether the audit was successful or not. You can find the fee schedule here.
- Development costs: The development team will incur significant costs in implementing the TR requirements. You should, of course, also factor in the associated costs.
- Consulting costs: It is advisable to work with a team that has already successfully completed the BSI certification process for other DiGA. This can often save you weeks of work thanks to practical insights. The costs for this are relatively manageable, but should be factored in.
At QuickBird Medical, we support companies in all technical and organizational aspects of BSI certification. Among other things, we have received one of the first three BSI certificates ever with our DiGA “Oriko®” which we developed ourselves. We will help you get through the certification process efficiently and securely. Please feel free to contact us.
4.2 Time Frame for the Certification Process
The certification process and thus also the schedule can be divided into the three phases mentioned above:
- Preparation phase: This is where your development team implements the BSI requirements. How quickly you can do this depends on many factors (the developers’ expertise, the current state of the system in terms of security, the number of developers, etc.).
- Test phase: The time frame here depends heavily on the testing agency and the quality of your documentation and product implementation. You should expect to wait at least 4 to 6 weeks before you receive a test report.
- Certification phase: Once the testing agency has sent the test report for your product to the BSI, the certification phase begins. The official BSI website states that this takes three weeks. However, in our experience, it is currently more realistic to expect this to take six weeks.
5. Validity Period & Recertification according to BSI TR-03161
A certificate issued by the BSI in accordance with technical guidelines is valid for a limited period of time. As a rule, the validity period of a product certificate is five years.
Different terms are only possible if this is expressly specified in the respective certification program. Validity is also always limited to the specific product version that has been tested and to the underlying version of the technical guideline.
If the conformity of a product cannot be confirmed after expiry of the validity period or after significant safety-related changes without re-testing, recertification is required. This involves re-testing the product to ensure that it meets the requirements of the TR. The scope of the test may be limited to the modified parts, provided that previous test results are still valid.
According to the official quote from the BSI here,recertification should be applied for no later than three months after the existing certificate expires (it remains to be seen whether the BfArM will agree to this for DiGA). Upon successful completion, a new certificate will be issued for the modified product version.
6. BSI TR-03161 Certificate with Conditions
A certificate in accordance with BSI TR-03161 is usually valid for up to five years. In individual cases, however, the BSI may, as part of its certification decision, impose additional conditions in the form of requirements that must be implemented by the manufacturer within a defined period of time.
In practice, this means that a certificate can be issued with a validity of a few months until certain requirements have been met. In this case, the manufacturer initially receives a valid certificate (with conditions), but is obliged to implement and verify the specified conditions within the specified period. If these conditions are not met, the certification can be revoked. If the conditions are demonstrably fulfilled within the deadline, a regular certificate without conditions is then issued.
This approach makes it possible to follow up on isolated deviations later on, for example, so as not to block the DiGA application process (or be rejected by the BfArM). However, a BSI certificate with conditions requires comprehensive implementation of all BSI TR-03161 requirements by the DiGA manufacturer. Certification remains extremely challenging and should not be underestimated under any circumstances.
7. Changes to Certified Products – BSI TR-03185
A certificate is only valid for the product version tested as part of the conformity assessment. Any changes to the product, such as further development, updates, patches or hotfixes, initially result in a new version for which the existing certificate is no longer automatically valid. Whether and how these changes are handled in terms of certification depends on their impact on TR conformity.
If an impact on conformity cannot be ruled out, recertification is required. However, if the changes are minor and an impact on conformity can be clearly ruled out, a maintenance procedure may be considered. In this case, the existing certificate is extended to the new product version without the need for a complete conformity assessment. The decision on this is made by the BSI on the basis of change documentation and an impact analysis to be submitted by the manufacturer. The original term of the certificate remains unchanged.
Future handling of product changes – the new BSI TR-03185
Having every minor change approved by the BSI naturally makes the DiGA development process significantly less efficient. Especially when critical errors occur in a DiGA, it is important to fix problems quickly with hotfixes. The current process of having every change reviewed by the BSI does not seem suitable for this.
The BSI is therefore currently working on a fundamental rethink of how product changes are handled in DiGAs. The focus here is on the planned introduction of the BSI TR-03185 “Secure Software Lifecycle,” which is intended to address the update and change process for software products in a structured manner.
TR-03185 provides for an independent certification program in which conformity assessments are carried out by IT baseline protection auditors accredited by the BSI.
The idea behind it: DiGA manufacturers with additional certification according to BSI TR-03185 have proven that they have a secure software development process (or life cycle). These manufacturers should therefore be allowed to publish certain changes to the product without prior BSI testing.
It is envisaged that DiGA manufacturers with BSI TR-03185 certification will have to carry out significantly fewer test procedures for subsequent versions of their BSI TR-03161-certified products. However, DiGA manufacturers are not explicitly required to obtain BSI TR-03185 certification. Implicitly, however, the smooth operation of a DiGA without TR-03185 certification will probably be difficult to achieve.
You can view the contents of BSI TR-03185 here: Link (BSI website)
Currently, no applications or certifications are possible. As things stand at present, the first certifications are expected in early 2026 at the earliest. However, the specific framework conditions for this are still being negotiated.
8. Practical Implications for DiGA
The requirements of BSI TR-03161 have a direct impact on the product as well as the development, operation, and further development of DiGAs. At QuickBird Medical, we have now fully implemented the BSI requirements in several DiGAs and, for example, received one of the first three BSI certificates for the DiGA “Oriko®”.
BSI certification has had many effects on our customer projects. We summarize some of them here:
- Changes after certification: Product modifications are significantly more complex later on, as a complex change process must be followed and approvals per release incur additional time and costs.
- Strongly regulated two-factor authentication: There are very high requirements for the implementation of two-factor authentication in DiGA. Depending on the implementation, these requirements can significantly impair the user-friendliness of DiGA. There are better and worse variants of implementation in terms of user-friendliness. (Please contact us if you need any input on this.)
- Short session durations and potentially frequent re-logins: The requirements of BSI TR-03161 mean that login and session times must be severely limited. Depending on the technical implementation, this can mean that users have to log in again relatively frequently, which can noticeably impair the user-friendliness of the DiGA. Here, too, there are ways to solve the problem in a way that has less impact on the user. (Please contact us if you need input on this.)
- Increased development effort: Architecture, implementation, testing, and documentation require significantly more effort than for non-regulated applications.
- Data loss in case of device loss:There are various ways to implement the TR requirements in a DiGA. Each has its advantages and disadvantages. With certain authentication options, it is virtually impossible to recover DiGA data if a user loses their cell phone, for example.
- Strict resilience requirements:Certain operating system versions and device configurations are excluded, such as older Android versions or activated developer mode, even though these are still widely used by a significant proportion of users. On the one hand, this is understandable from a security perspective, but it means that up to 10% of your target group, for example, cannot access the DiGA.
- Limited hotfix capability:Short-term bug fixes are officially only possible with approval from the BSI, which makes it difficult to respond quickly. This is set to improve in the future thanks to additional certification in accordance with TR-03185, which means that certain changes may no longer require approval.
9. Mandatory Penetration Testing for DiGA
The obligation to perform a penetration test (“pen test”) does not arise from BSI TR-03161. It stems from the legal framework of the DiGA Regulation (DiGAV). This stipulates that every DiGA must provide evidence of a current penetration test in order to meet the data security requirements in accordance with Annex 1 DiGAV.
With the new DiGA guidelines dated December 10, 2025, the BfArM takes a concrete position on this issue: Certification according to TR-03161 eliminates the need for an additional pen test for the approval of a DiGA.
10. BSI TR-03161 vs. ISO 27001
In order for a DiGA to be listed in the BfArM directory, the manufacturer must submit both ISO 27001 certification and BSI TR-03161 certification. Both relate to information security. So why two certifications?
The reason for this lies in the focus of these two standards.
ISO 27001 is purely a management standard: it defines how a comprehensive information security management system (ISMS) is set up, operated and continuously improved within a company. Certification is therefore granted for the Company and its processes,not a single product. There is no product-related testing, no architecture review and no analysis of source code or specific security measures of a product.
BSI TR-03161, on the other hand, is a technical product certification specifically for digital health and care applications. It sets out very specific technical and organizational security requirements and checks whether the individual product (including app, backend, interfaces) meets them. This makes it significantly more specific, stricter and more product-oriented than ISO 27001. The BSI TR-03161 serves as the legal basis for DiGA and DiPA approvals in Germany.
| Category | ISO 27001 | BSI TR-03161 |
| Type of Standard | Management standard | Technical product safety guideline |
| Certification Object | Company or ISMS | Specific product (app, backend, web portal) and specifically specific product version |
| Focus | Processes, governance, risk management | Technical security requirements, architecture, implementation |
| Scope | Company-wide, regardless of products | Product-related and mandatory for DiGA/DiPA |
| Technical Tests | No specific product tests | Detailed technical tests including cryptography, APIs, hosting |
| Source Code Analysis | Not included | An integral part of the audit |
| Requirements | Abstract, process-oriented | Concrete, detailed specifications for products and processes |
| Objective | Establishment of an ISMS | Secure operation and development of a healthcare application |
11. Criticism of the Process
Both the obligation to obtain certification in accordance with BSI TR-03161 and the resulting very strict requirements are heavily criticized by many parties. Frequently mentioned points include:
- Limitations in user-friendliness: Multi-level security mechanisms and strict requirements can significantly impair usability. It is emphasized that this makes it more difficult for patients to access digital health services.
- Limited accessibility for relevant target groups: The very restrictive device and system requirements of BSI TR-03161 exclude many end devices. Older people and people with physical or cognitive impairments in particular often use devices that do not meet these requirements and are therefore not accepted. As a result, a significant proportion of the relevant target group is excluded from using digital health applications.
- High implementation and documentation costs: According to numerous manufacturers, the highly detailed safety and process requirements lead to considerable additional development and documentation work. Months of additional work complicate and prevent such new innovations.
- Rising costs for providers: Both the certification itself and the ongoing verification of compliance incur enormous costs for DiGA manufacturers. These costs are difficult or impossible to finance, especially for small businesses.
- Uncertainty regarding requirements: In many areas of TR-03161, it is unclear what the BSI considers to be the correct implementation. In some cases, individual requirements also contradict each other. As a result, DiGA manufacturers invest a lot of time in an implementation that may then be rejected by the BSI after long waiting periods.
- A national solo effort: Critics complain that BSI TR-03161 is a purely German security standard that is not harmonized with European requirements . This complicates international scaling and increases the regulatory burden on manufacturers.
Several industry representatives have highlighted these points in their statements and called for a more balanced solution between security, practicality, and economic feasibility (see, for example, here, here, and here).
It remains to be seen to what extent these points will be addressed in the future. The next update to BSI TR-03161, which is expected to be released in 2026, is particularly relevant here.
12. Important Links and Resources
12.1 General Information
Here you will find important resources relating to BSI certification:
- Links to the PDFs of BSI TR-03161 (see bottom of page): Link (BSI website)
- FAQ on BSI TR-03161: Link (BSI website)
- Information on TR certifications at the BSI: Link (BSI website)
- Links to the PDFs of BSI TR-03161 (Secure Software Lifecycle): Link (BSI website)
12.2 List of Applications already certified according to TR-03161
You can conveniently filter for BSI-certified DiGA in our DiGA Directory Analyzer, view the respective DiGA testing center, and compare other attributes: DiGA Directory for Manufacturers (including BSI certifications)
The official list of digital health applications (including applications prior to listing) that have already received a certificate from the BSI can be found here: Official list of certified applications
12.3 List of Testing Centers for BSI TR-03161
Here you will find a list of testing laboratories accredited by the BSI: List of accredited TR testing laboratories
If you search for “03161” on the page, you will find all the places that can accompany your certification according to BSI TR-03161.
13. Future Outlook for BSI TR-03161 and DiGA Data Security Certification
Data security requirements for DiGAs are currently evolving and will be further specified in the coming years. Three relevant developments in particular are emerging that DiGA manufacturers should plan for at an early stage.
- Update of BSI TR-03161: An update to TR-03161 has been announced for the coming year. It is expected that practical experience gained from previous applications will be incorporated and that individual requirements will be clarified or adapted.
- Introduction of BSI TR-03185 for secure software lifecycle: In addition to TR-03161, a new certification for the entire software lifecycle is in preparation with the TR-03185. The aim is to map update and change processes more systematically and, in the long term, to reduce the effort required for recurring recertifications in subsequent versions.
- Data protection certification: In addition to data security, data protection certification is also planned for DiGA (and has already been enshrined in law). Once a testing process and testing bodies have been established for this purpose, the BfArM will require DiGA manufacturers to obtain this certification.
14. Conclusion
For DiGAs, the number of mandatory certifications appears to be rising steadily: medical device approval or certification, ISO 27001, BSI TR-03161, and future certifications such as BSI TR-03185 (not mandatory, but seemingly unavoidable) and the data protection certificate for DiGA.
This leads to increasing regulatory complexity, which places a heavy burden on smaller manufacturers in particular. The budget required to prepare, implement, and continuously maintain these certifications is currently growing steadily. In our view, there is a risk that this will slow down or even prevent the speed of innovation and market entry of new solutions.
Nevertheless, with the right strategy (and sufficient budget), the whole thing is still feasible. We have learned to deal with complexity in our DiGA projects and have gained a lot of knowledge that we are happy to pass on. Particularly with regard to BSI TR-03161 certification, there is a lack of clear official guidelines for the implementation of some requirements. To ensure that not every manufacturer has to learn these lessons from scratch, we advise manufacturers on the implementation of BSI requirements.
If you need a partner to implement your DiGA, fulfill BSI requirements and take care of all other regulatory obligations for you, please feel free to contact us.. We have already been involved in the implementation of over 15 different DiGA projects and have the necessary certificatesto bring your DiGA to market safely. You can find more information on this here.